Creating IAM Roles on AWS¶
Here is an example of how to set up IAM roles on AWS Management Console.
- Navigate to the
IAMservice on AWS Management Console. -
Create a new IAM policy:
- Click
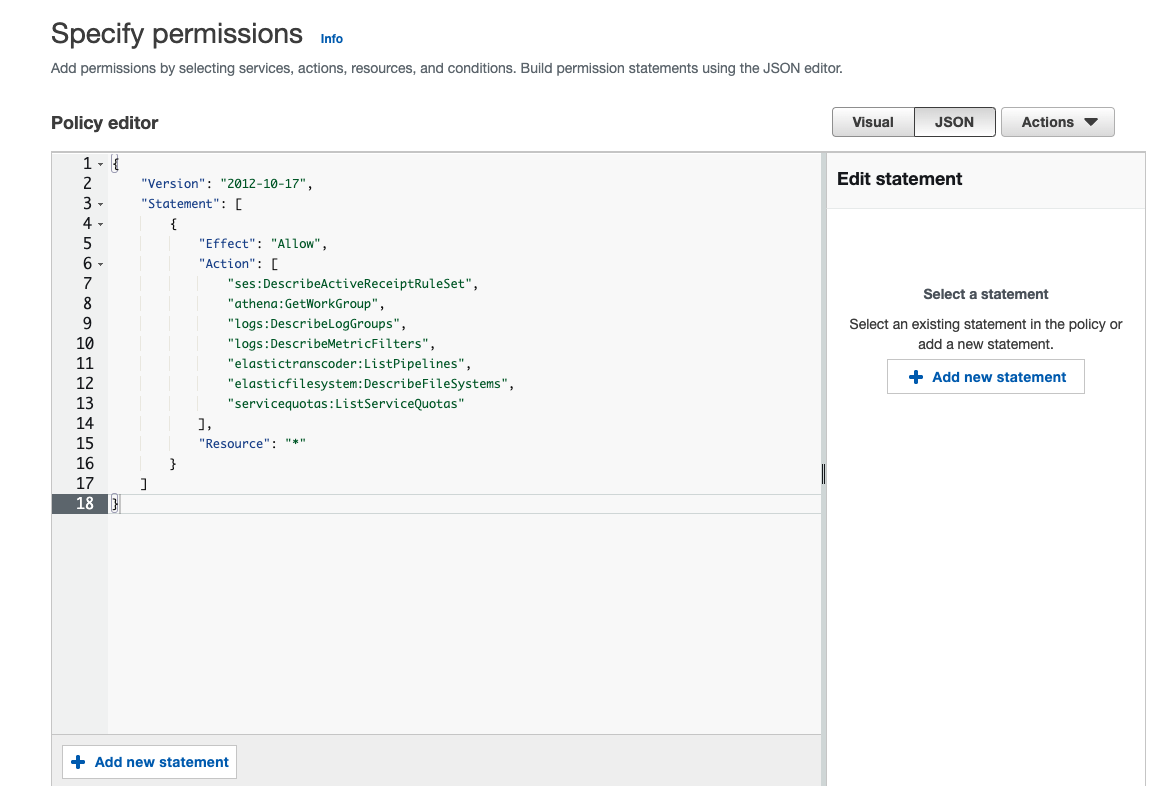
Create Policyin the IAM policy menu. - Open the
JSONtab and paste the following policy. ClickReview Policy.{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "ses:DescribeActiveReceiptRuleSet", "athena:GetWorkGroup", "logs:DescribeLogGroups", "logs:DescribeMetricFilters", "elastictranscoder:ListPipelines", "elasticfilesystem:DescribeFileSystems", "servicequotas:ListServiceQuotas" ], "Resource": "*" } ] } - Enter
RISKENin the name field and clickCreate Policy.
- Click
-
Create a new IAM role:
- Click
Create Rolein the IAM role menu. - Select
AWS accountforSelect type of trusted entityand enter the following:- AWS account: Another AWS account
- Account ID: You need to register the AWS account ID for RISKEN as a trusted entity.
AWS account ID
Please contact your system administrator for the AWS account ID in the RISKEN environment.
- External ID:
{External ID generated earlier} 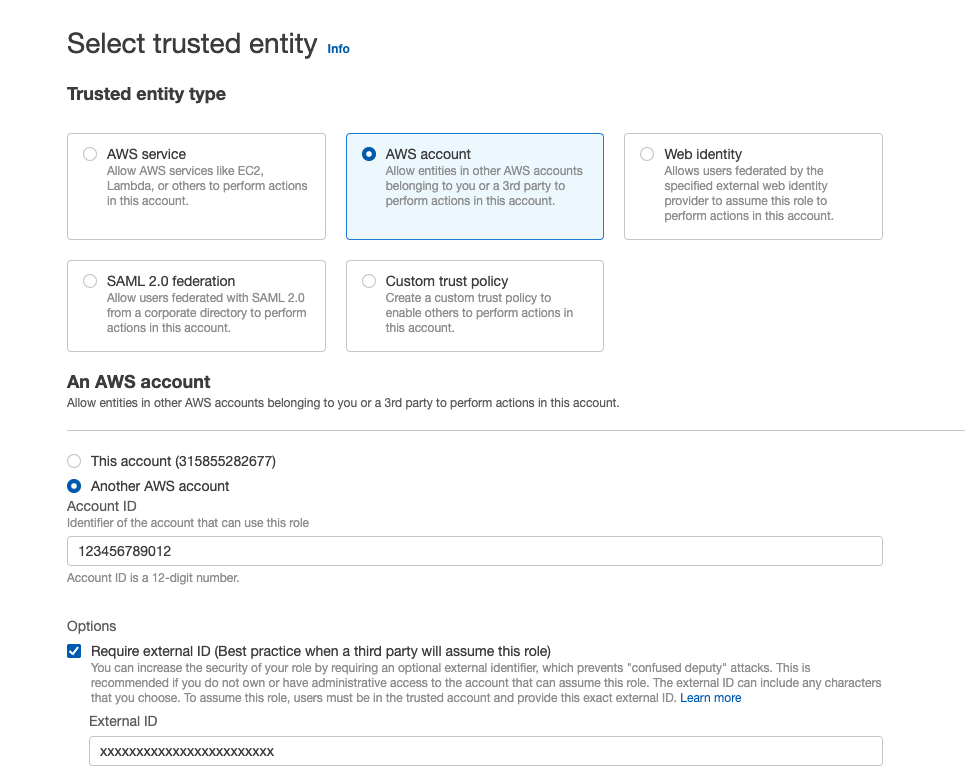
- Click
Next: Permissions.
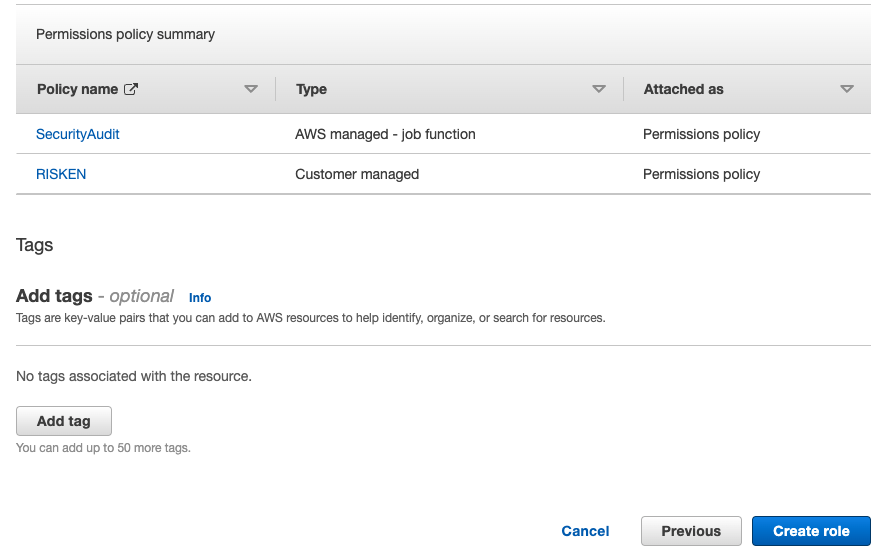
- On the Permissions screen, search for and check the following two policies, then click
Next: Tags:RISKEN(the policy created earlier)SecurityAudit(the management policy)
- Click
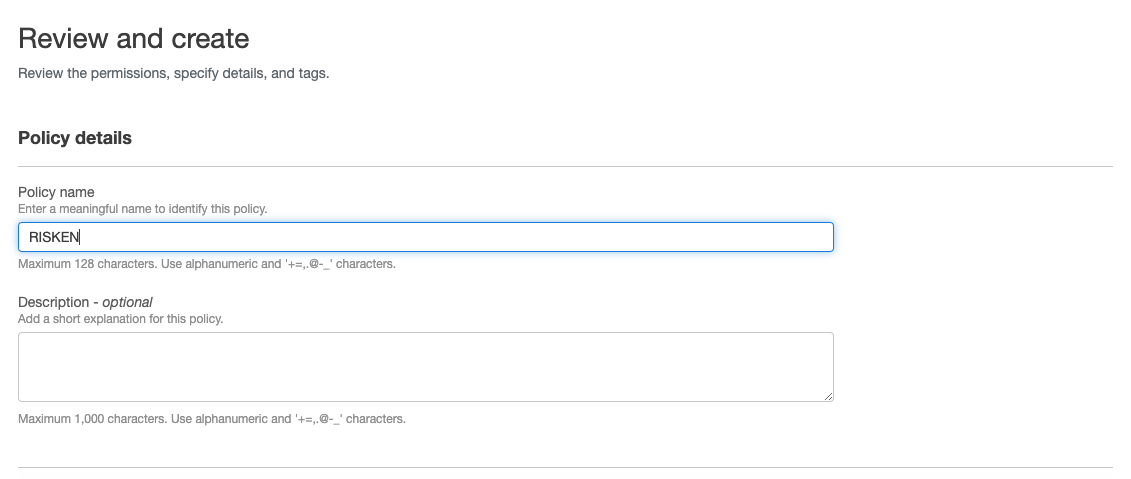
Next: Tags. - On the Review screen, enter
RISKENin the Role name field and clickCreate Role.
- Click