Automating Security Reviews¶
At RISKEN, we offer RISKEN Security Review, a tool for automating source code reviews.
The tool is executed upon GitHub pull requests, detecting potentially dangerous code that could lead to cyber attacks such as secret commits or injections, and provides review comments on the pull requests.

Mechanism
RISKEN Security Review runs as a GitHub Actions (Custom Action). It is also available in the following MarketPlace.
Features¶
The main features of RISKEN Security Review are:
- Commenting on PRs
- Secret commits
- Code with security issues
- Fast operation
- Works faster compared to similar code review tools
- Runs a built and lightweight container
- Scans only the changed parts, not the entire code
- Checks out only the HEAD, allowing it to work on large repositories
- Small changes can be completed in about 10 to 60 seconds
Setting Up on Individual Repositories¶
Operates by creating a GitHub Actions workflow file.
- Create a file named
.github/workflows/security-review.yamlin the target repository - Copy & paste the following code into the created file
name: Security Code Review on PR
on:
pull_request:
types: [opened, synchronize]
jobs:
review:
runs-on: ubuntu-latest
permissions:
contents: read
pull-requests: write
steps:
- uses: actions/checkout@v4
- uses: ca-risken/security-review@v1
with:
github_token: ${{ secrets.GITHUB_TOKEN }}
Integration with RISKEN Environment¶
The above setup works on its own, but you can optionally integrate it with an existing RISKEN environment.
- Integrating with RISKEN offers the following benefits:
- Access to generated AI explanations and recommended comments
- Detailed scan results including severity, score, and related links
- Share with the security team for expert advice
- To enable integration with RISKEN, add the following options:
risken_console_urlrisken_api_endpointrisken_api_token
- The final workflow file will look like below (sample)
To run this JOB, you need to register secrets that GitHub Actions can reference in advance.
| Parameter | Key | Description | Required | Default | Examples |
|---|---|---|---|---|---|
risken_console_url |
RISKEN_CONSOLE_URL |
RISKEN Console URL | no |
https://console.your-env.com | |
risken_api_endpoint |
RISKEN_API_ENDPOINT |
RISKEN API Endpoint | no |
https://api.your-env.com | |
risken_api_token |
RISKEN_API_TOKEN |
RISKEN API Token | no |
xxxxx |
You need to issue an access token beforehand
You need to issue an access token for the relevant RISKEN project.
Applying to the Entire Organization¶
If you are an organization administrator, in addition to setting up individual repositories, you can enable code review for the entire organization.
- Create a
.githubrepository within the organization (use an existing one if already created)- The
.githubrepository is a special repository for storing common templates and workflows - However, any other repository is also fine
- The
- Register RISKEN information in the organization settings(
optional)- Save
RISKEN_CONSOLE_URLin Organization secrets (Visibility is All repositories) - Save
RISKEN_API_ENDPOINTin Organization secrets (Visibility is All repositories) - Save
RISKEN_API_TOKENin Organization secrets (Visibility is All repositories)- You need to issue an Access Token in the RISKEN environment beforehand
- Save
- Create the following workflow file in the
.githubrepository - Create
rulesetsin the organization settings- What are rulesets?
- Create a new
New branch rulesetin rulesets - Specify the target repositories and branches (the following settings target all repositories' default branches)
- Specify
All Repositories - For branches, choose
Include default branches
- Specify
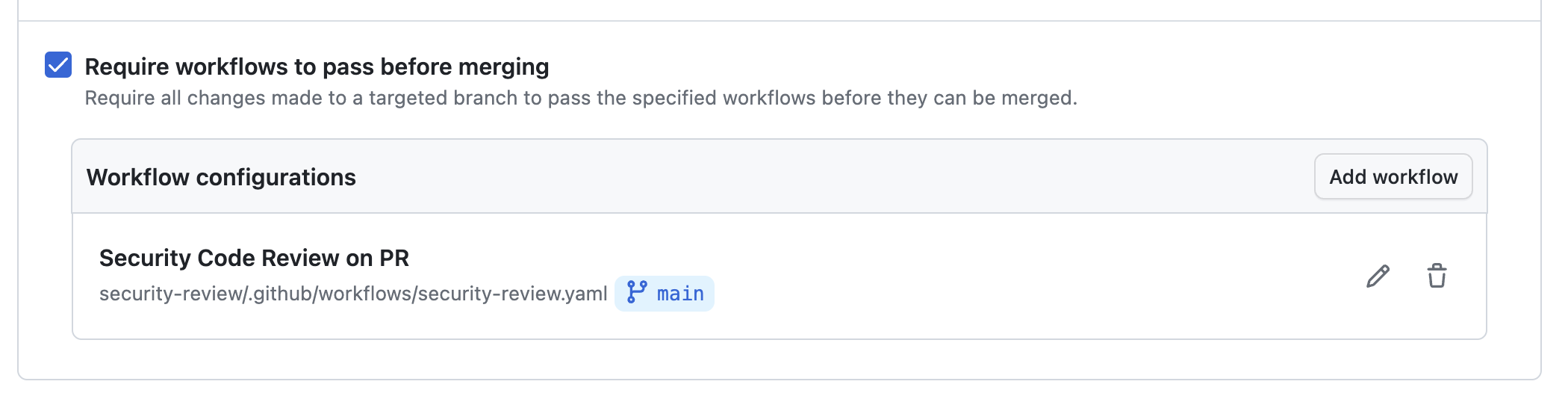
- Check
Require workflows to pass before mergingand specify the workflow file created above- Specify the repository as
.github - Specify the version as the master branch (like
masterormain)- Specifying a particular version (branch, tag, commit SHA) is also possible
- Specify the workflow file as
.github/workflows/security-review.yaml
- Specify the repository as
About Repository Visibility
- In these steps, we used the
.githubrepository, but if there are public repositories within the organization, there may be issues with referencing the workflow file- This is because public repositories can only reference public workflow files
- Making the
.githubrepository public solves this issue, but if you have templates, workflows, or profile data that cannot be published, prepare another repository
- For details, refer to workflow settings
Workflow File (Sample)¶
Save the following as a file named .github/workflows/security-review.yaml (yaml file name is arbitrary)
name: Security Code Review on PR
on:
pull_request:
types: [opened, synchronize]
jobs:
review:
runs-on: ubuntu-latest
permissions:
contents: read
pull-requests: write
steps:
- uses: actions/checkout@v4
- uses: ca-risken/security-review@v1
with:
github_token: ${{ secrets.GITHUB_TOKEN }}
risken_console_url: ${{ secrets.RISKEN_CONSOLE_URL }}
risken_api_endpoint: ${{ secrets.RISKEN_API_ENDPOINT }}
risken_api_token: ${{ secrets.RISKEN_API_TOKEN }}